Generic SAML 2.0
Cloudflare Zero Trust integrates with any identity provider that supports SAML 2.0. If your identity provider is not listed in the integration list of login methods in Zero Trust, it can be configured using SAML 2.0 (or OpenID if OIDC based). Generic SAML can also be used if you would like to pass additional SAML headers or claims for an IdP in the integration list.
Minimum requirements for identity providers:
- The IdP must conform to SAML 2.0.
- The IdP must provide a Single sign-on URL, an Entity ID or Issuer URL, and a Signing certificate.
- The IdP must include the signing public key in the SAML response.
Most identity providers allow users to create an Application. In this context, an application is a set of parameters that the identity provider will then pass on to Cloudflare to establish an integration.
The typical setup requirements are:
- Create a new integration in the identity provider with the type set as SAML.
- Set both the Entity/Issuer ID and the Single sign-on URL to:
You can find your team name in Zero Trust under Settings > Custom Pages.https://<your-team-name>.cloudflareaccess.com/cdn-cgi/access/callback
- Set the Name ID/Email format to
emailAddress. - (Optional) Set the signature policy to Always Sign.
If your identity provider supports metadata file configuration, you can use the default or identity provider specific metadata endpoint:
- Default:
https://<your-team-name>.cloudflareaccess.com/cdn-cgi/access/saml-metadata - Identity provider specific:
https://<your-team-name>.cloudflareaccess.com/cdn-cgi/access/<identity-provider-id>/saml-metadata, where<identity-provider-id>is theidvalue obtained from List Access identity providers. Use this endpoint if your IdP requires a configuration not defined in the default metadata file.
To download the SAML metadata file, copy-paste the metadata endpoint into a web browser and save the page as an .xml file. Upload this XML file to the identity provider.
- In Zero Trust ↗, go to Settings > Authentication > Login methods.
- Select Add new and select SAML.
- Choose a descriptive name for your identity provider.
- Enter the Single Sign on URL, IdP Entity ID or Issuer URL, and Signing certificate obtained from your identity provider.
- (Optional) To enable SCIM, refer to Synchronize users and groups.
- (Optional) Under Optional configurations, configure additional SAML options.
- Select Save.
You can now test the IdP integration. A success response should return the configured SAML attributes.
The generic SAML integration allows you to synchronize user groups and automatically deprovision users using SCIM.
Your identity provider must support SCIM version 2.0.
-
In Zero Trust ↗, go to Settings > Authentication.
-
Find the IdP integration and select Edit.
-
Turn on Enable SCIM.
-
(Optional) Configure the following settings:
- Enable user deprovisioning: Revoke a user's active session when they are removed from the SCIM application in IdP. This will invalidate all active Access sessions and prompt for reauthentication for any WARP session policies.
- Remove user seat on deprovision: Remove a user's seat from your Zero Trust account when they are removed from the SCIM application in IdP.
- SCIM identity update behavior: Choose what happens in Zero Trust when the user's identity updates in IdP.
- Automatic identity updates: Automatically update the User Registry identity when IdP sends an updated identity or group membership through SCIM. This identity is used for Gateway policies and WARP device profiles; Access will read the user's updated identity when they reauthenticate.
- Group membership change reauthentication: Revoke a user's active session when their group membership changes in IdP. This will invalidate all active Access sessions and prompt for reauthentication for any WARP session policies. Access will read the user's updated group membership when they reauthenticate.
- No action: Update the user's identity the next time they reauthenticate to Access or WARP.
-
Select Save.
-
Copy the SCIM Endpoint and SCIM Secret. You will need to enter these values into IdP.
The SCIM secret never expires, but you can manually regenerate the secret at any time.
Setup instructions vary depending on the identity provider. In your identity provider, you will either need to edit the original SSO application or create a new SCIM application. Refer to your identity provider's documentation for more details. For example instructions, refer to our Okta or JumpCloud guides.
If you would like to build policies based on IdP groups:
- Ensure that your IdP sends a
groupsfield. The naming must match exactly (case insensitive). All other values will be sent as a SAML attribute. - If your IdP requires creating a new SCIM application, ensure that the groups in the SCIM application match the groups in the original SSO application. Because SCIM group membership updates will overwrite any groups in a user's identity, assigning the same groups to each app ensures consistent policy evaluation.
To check if a user's identity was updated in Zero Trust, view their User Registry identity.
SAML integrations allow you to pass additional headers or claims to applications.
This optional configuration signs the Access JWT with the Cloudflare Access public key to ensure that the JWT is coming from a legitimate source. The Cloudflare public key can be obtained at https://<your-team-name>.cloudflareaccess.com/cdn-cgi/access/certs.
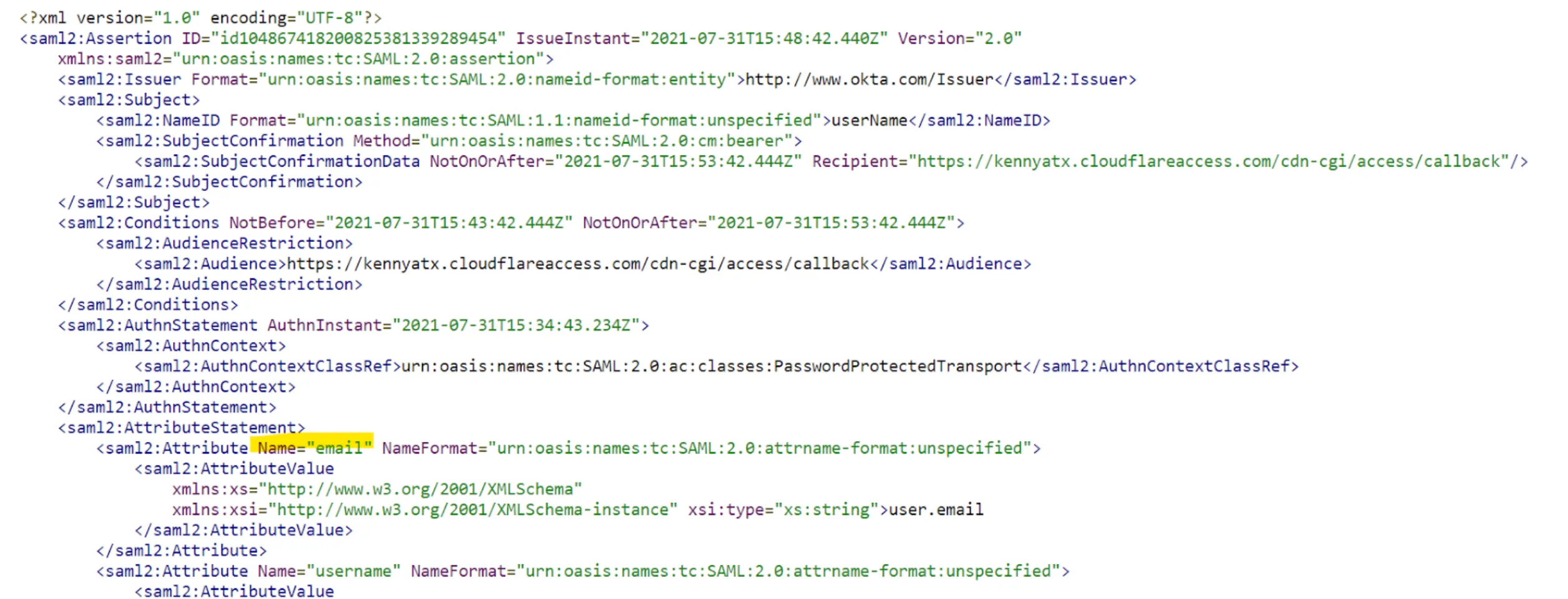
Many Access policies depend on a user's email address. Some identity providers have a different naming for the email address attribute (for example, Email, e-mail, emailAddress). This can typically be checked in the identity provider's SAML test option.
Example in Okta:
Cloudflare Access supports SAML (Security Assertion Markup Language) attributes and SAML headers for all SAML IdP integrations.
SAML attributes refer to specific data points or characteristics that the IdP shares about the authenticated user. These attributes often include details like email address, name, or role, and are passed along to the service provider upon successful authentication.
SAML headers are metadata in the SAML protocol communication which convey information about the sender, recipient, and the message itself. These headers can be leveraged to provide extra context or control over the communication.
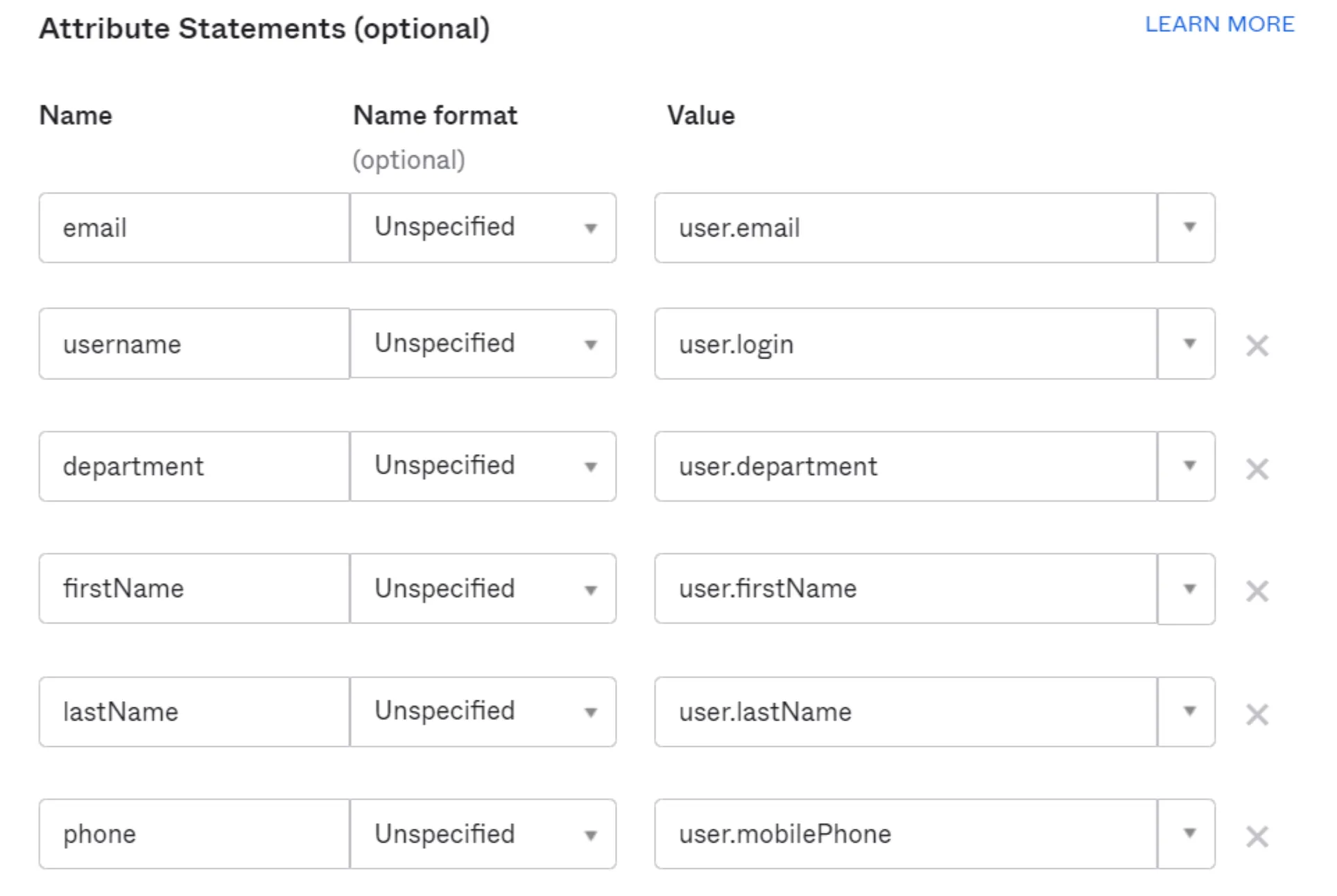
SAML attributes are added to the Access JWT. These attributes can then be consumed by self-hosted or SaaS applications connected to Access. Any SAML attribute configured in the SAML integration must also be sent from the IdP.
Example in Okta:
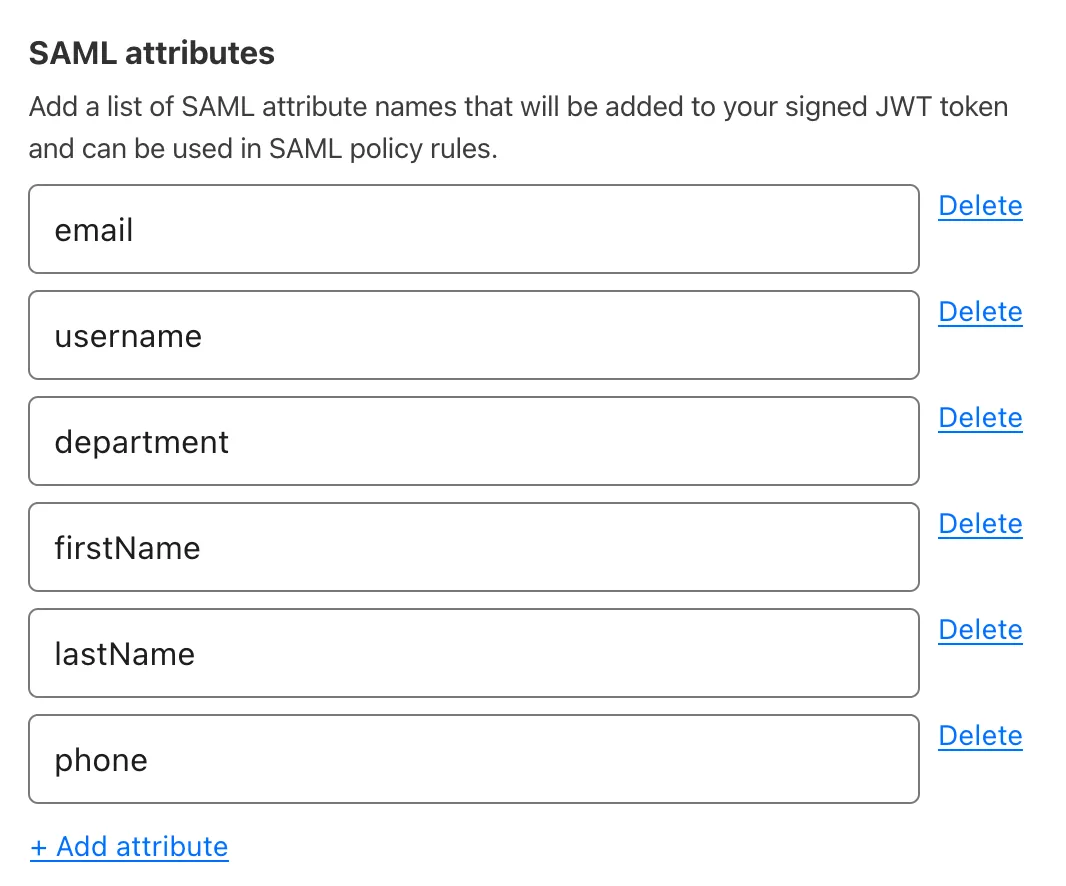
How to receive these SAML attributes in Cloudflare:
If an application specifically requires SAML attributes upon sign-in, then the attributes can be passed as headers. The Attribute name should be the value coming from your IdP (for example, department). You can assign any Header name to the attribute. The header name will appear in the response headers when Access makes the initial authorization request to https://<your-team-name>.cloudflareaccess.com/cdn-cgi/access/callback.
Cloudflare Access extends support for multi-record SAML attributes such as groups. These attributes are parsed out and can be individually referenced in policies. This feature enables granular access control and precise user authorization in applications.
Cloudflare Access does not currently support partial attribute value references.